AWS GPU instances are known for deep learning purposes but they can also be used for running video games. This tutorial goes through how to set up your own EC2 GPU optimised instance to run the top-selling and most played game “PlayerUnknown’s Battlegrounds (PUBG)”.
To get started, make sure you are in the AWS region closest to you, select Microsoft Windows Server to be the AMI and set the instance type to be g2.2xlarge. The instance is backed by Nvidia Grid GPU (Kepler GK104), 8x hardware hyper-threads from an Intel Xeon E5–2670 and 15GB of RAM.
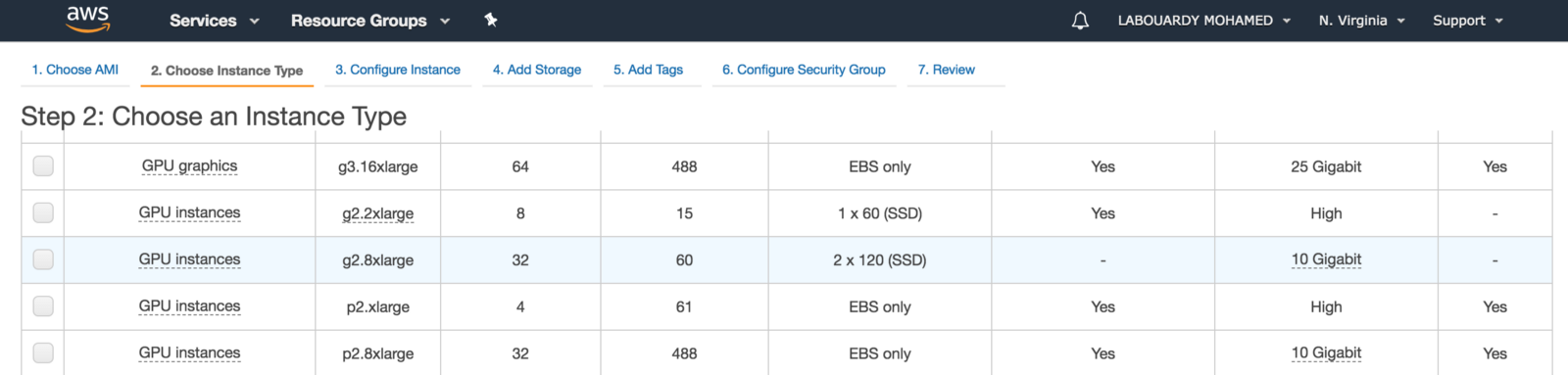
For games with resource-intensive, you should use the next generation of GPU instances: P2, P3 and G3 (have up to 4 NVIDIA Tesla M60 GPUs).
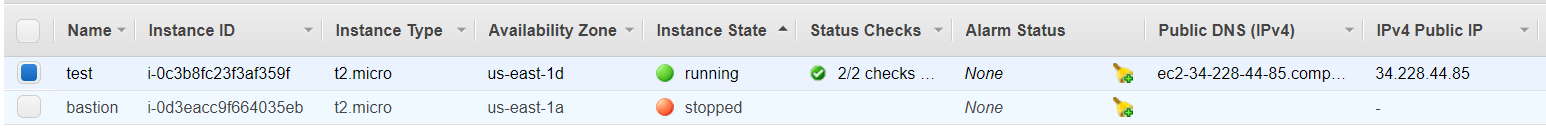
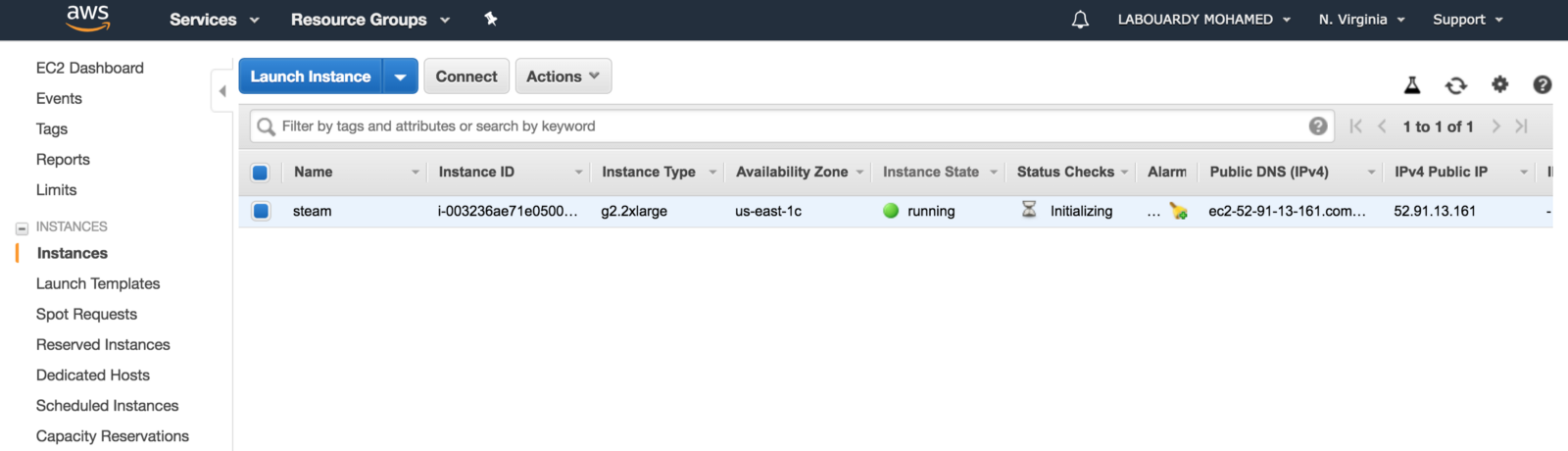
After this is done, click on “Launch Instances”, and you should see a screen showing that your instance is been created:
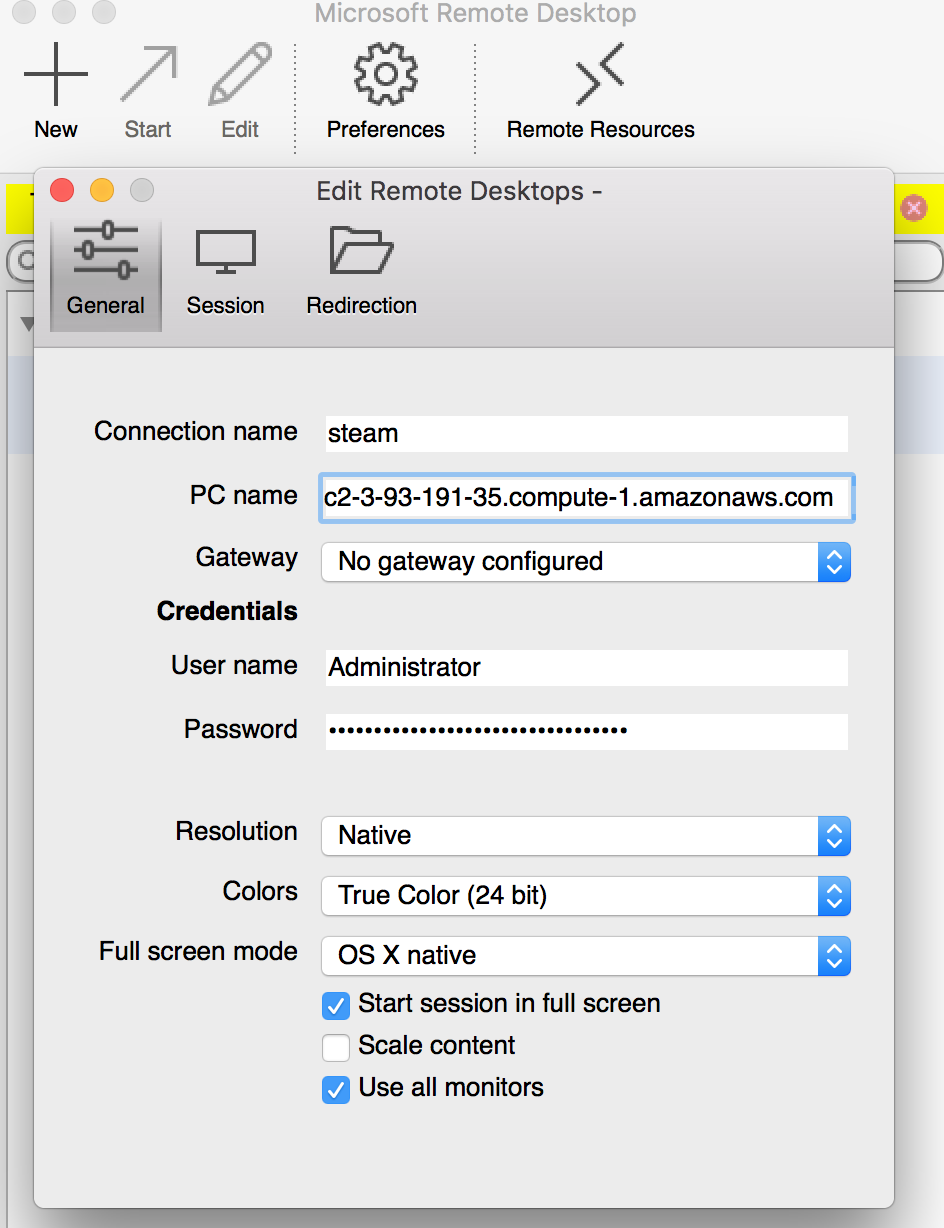
To connect to your Windows instance, you must retrieve the initial administrator password and specify this password when you connect to your instance using Remote Desktop:
Before you attempt to log in using Remote Desktop Connection, you must open port 3389 on the security group attached to your instance
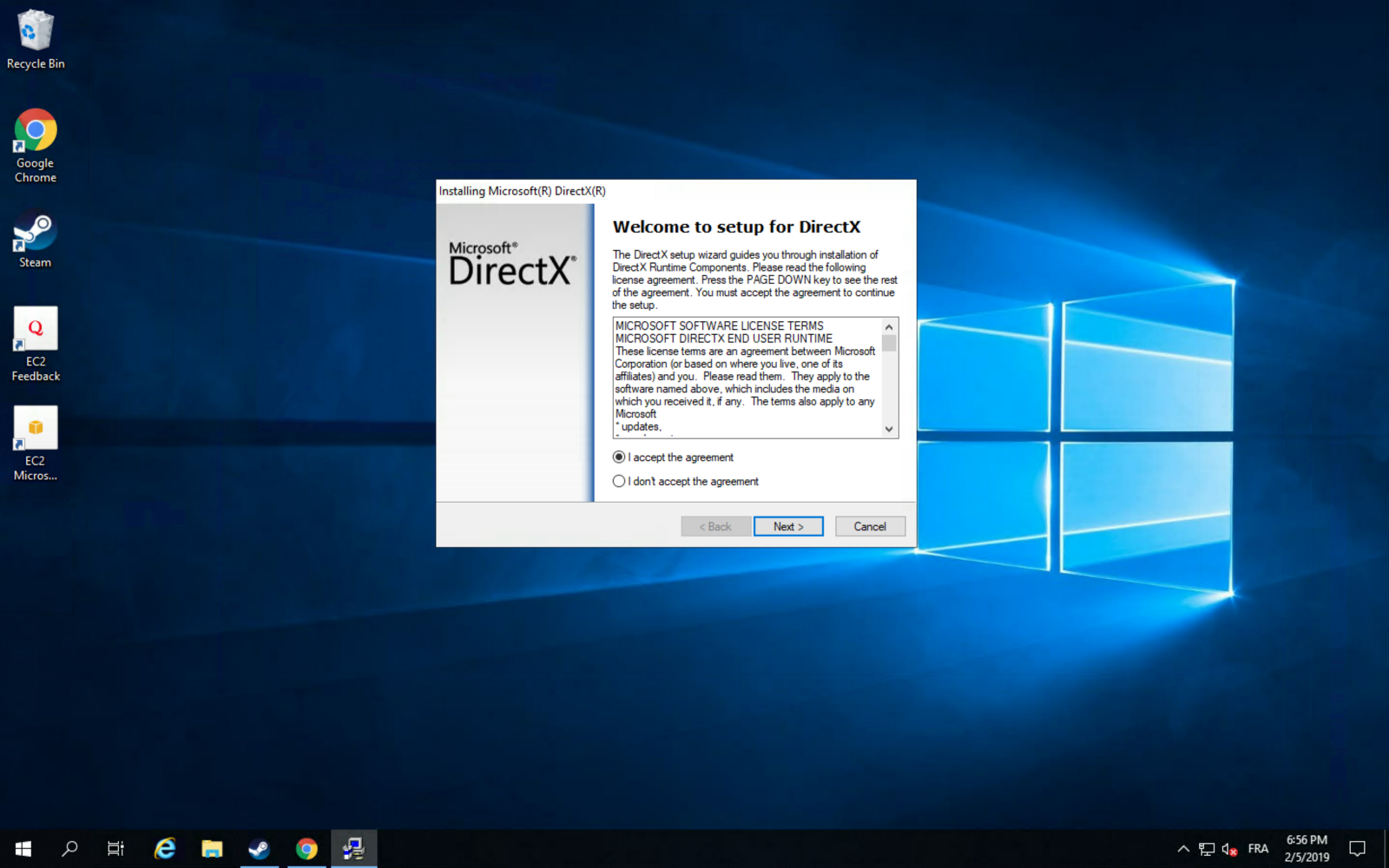
After you connect, install Microsoft Direct X11 after installing Chrome (it saves a lot of time):
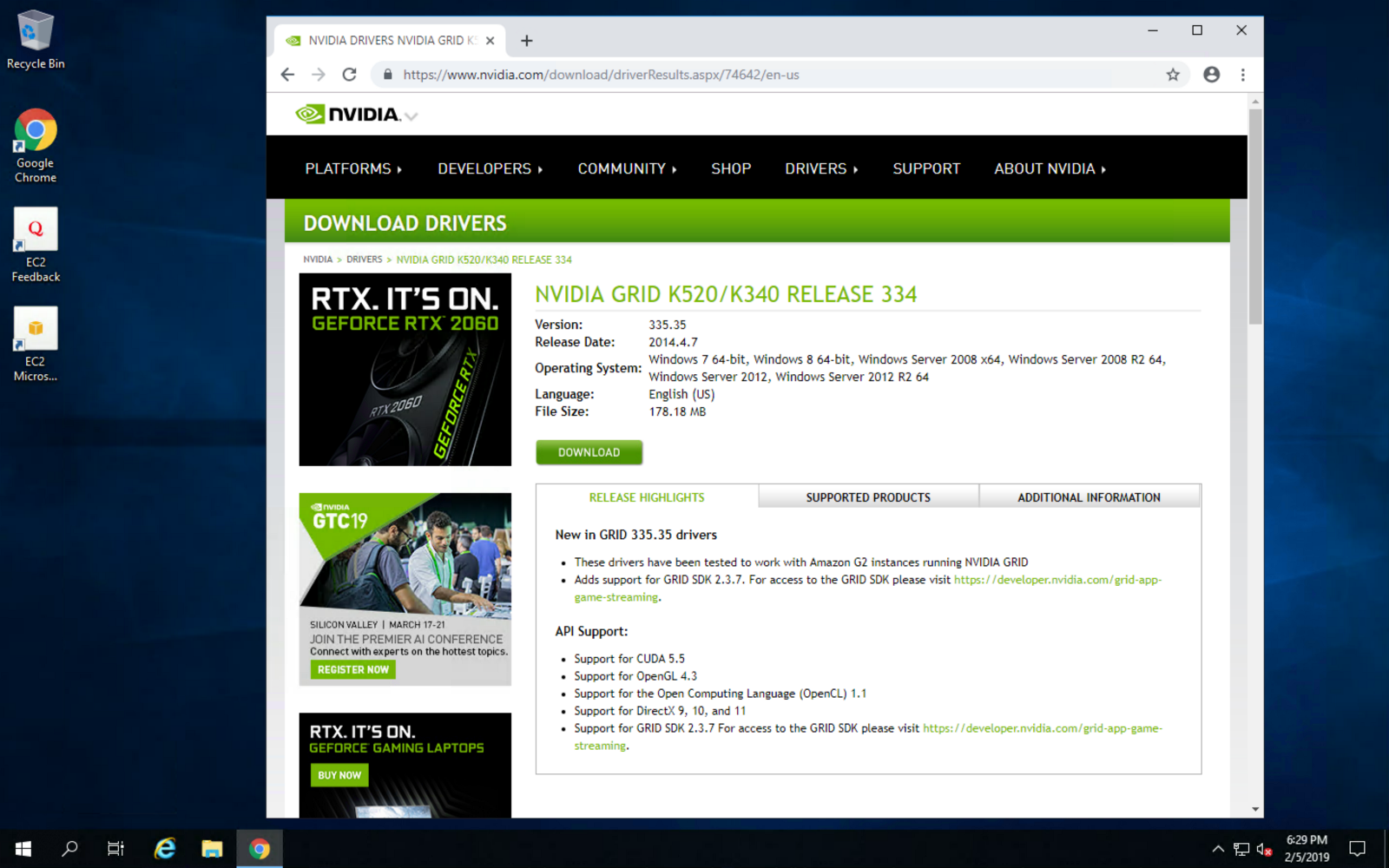
Next, install the graphic driver for maximum gaming performance:
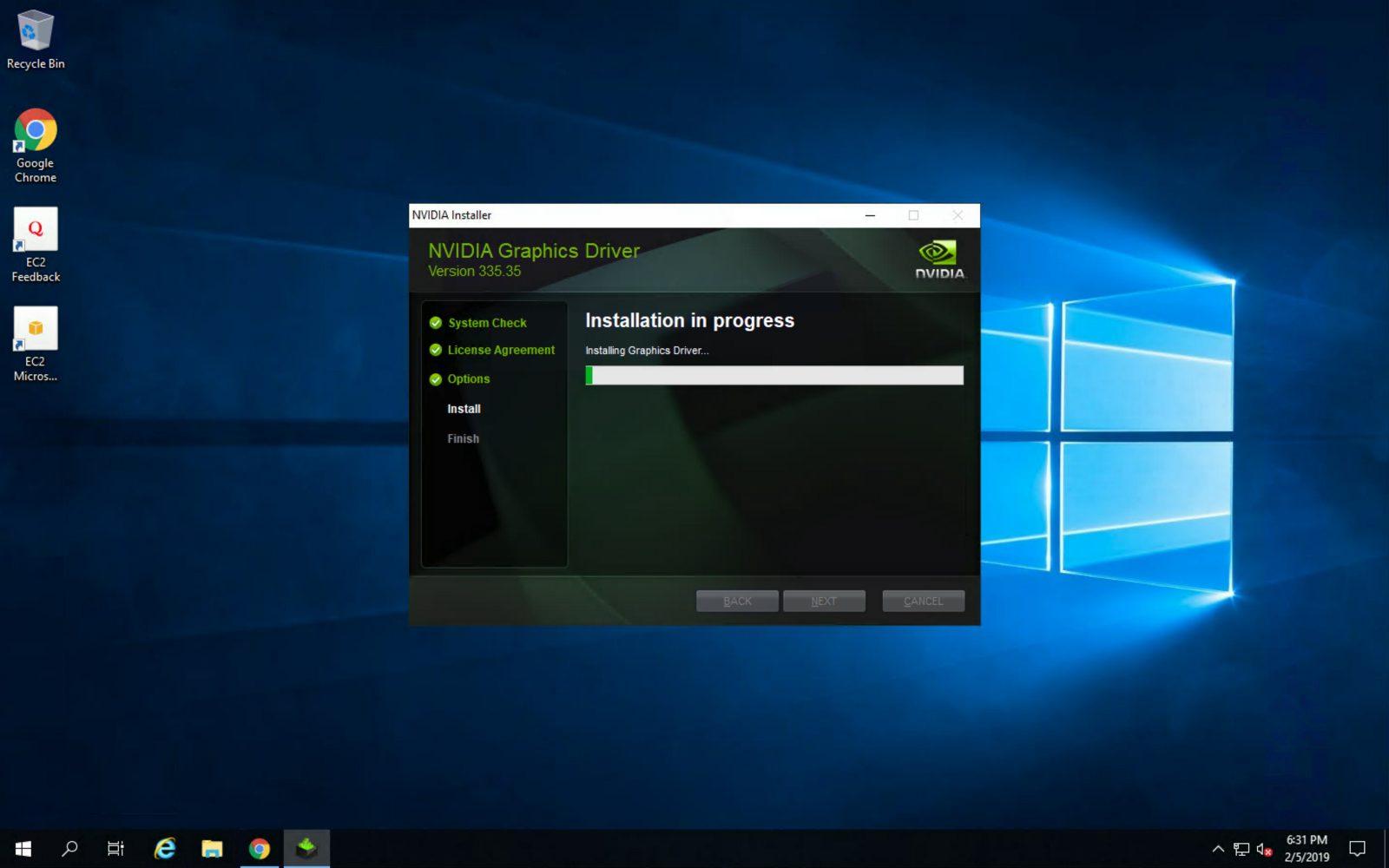
Once installed, make sure to reboot the instance for changes to take effect:
Then, install Steam, login using your account and install PUBG from the “Library” section:
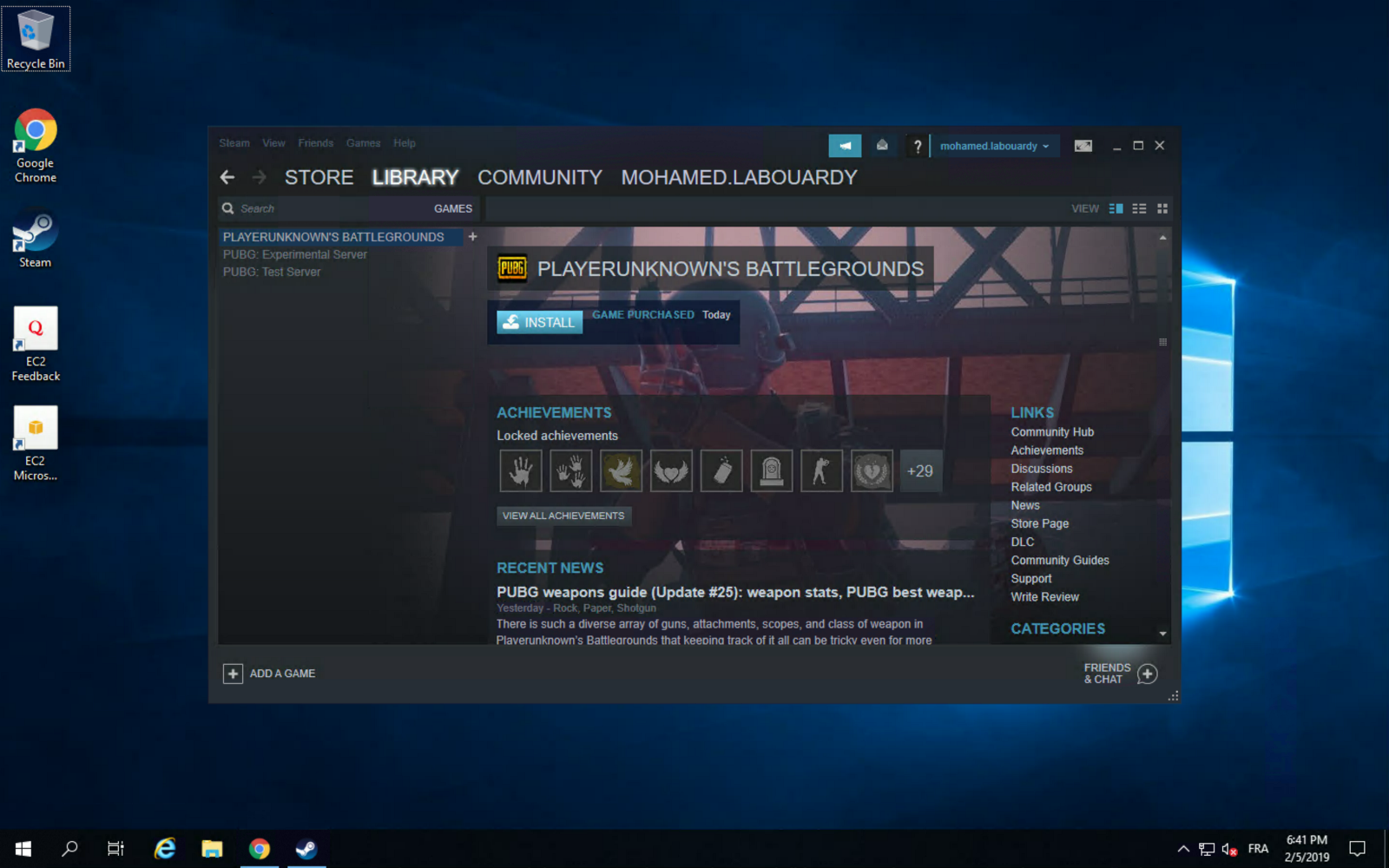
You can take advantage of AWS high network performance (up to 10 Gbps of bandwidth):
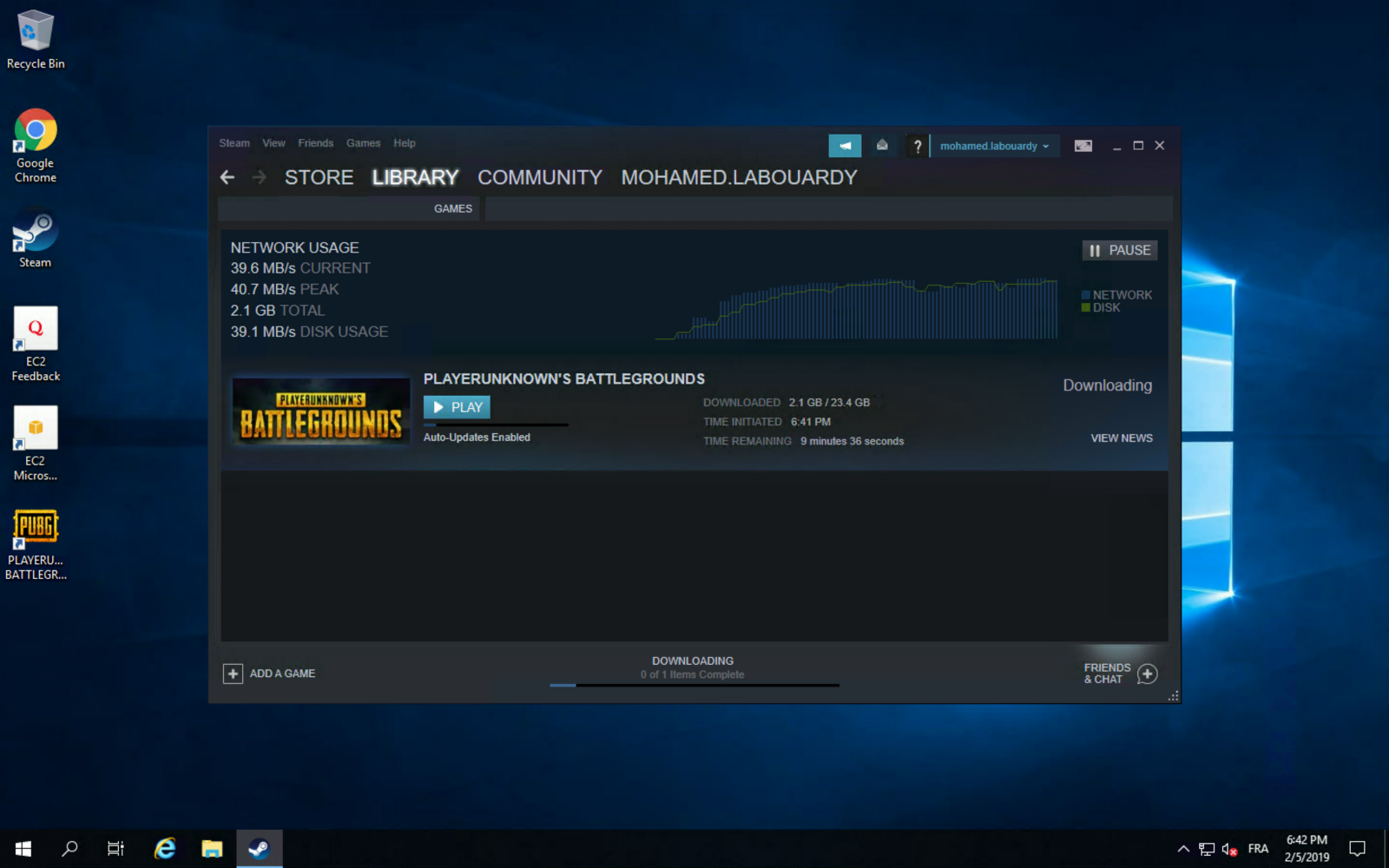
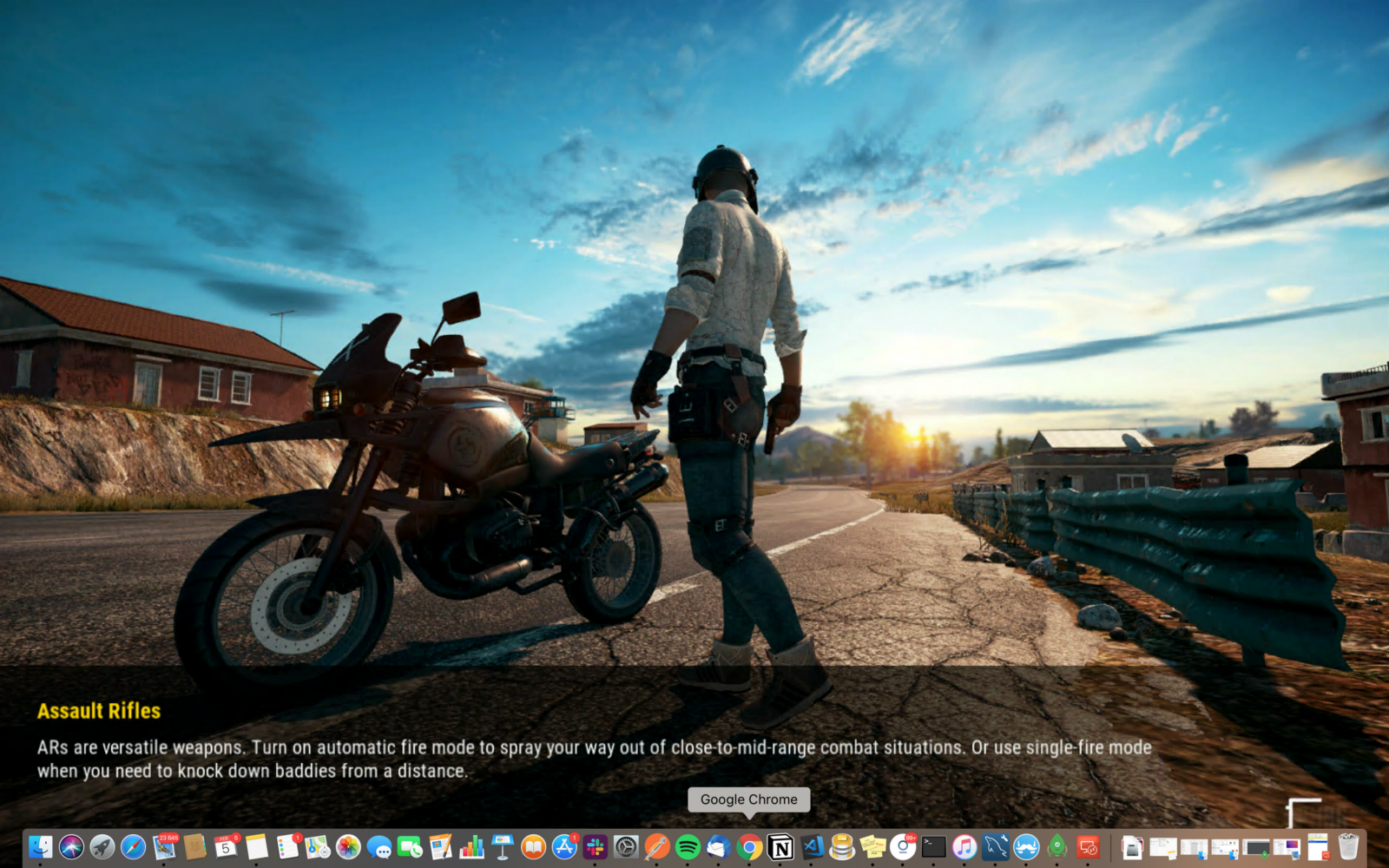
Once the game is installed, you can play PUBG on your virtualized GPU instance:
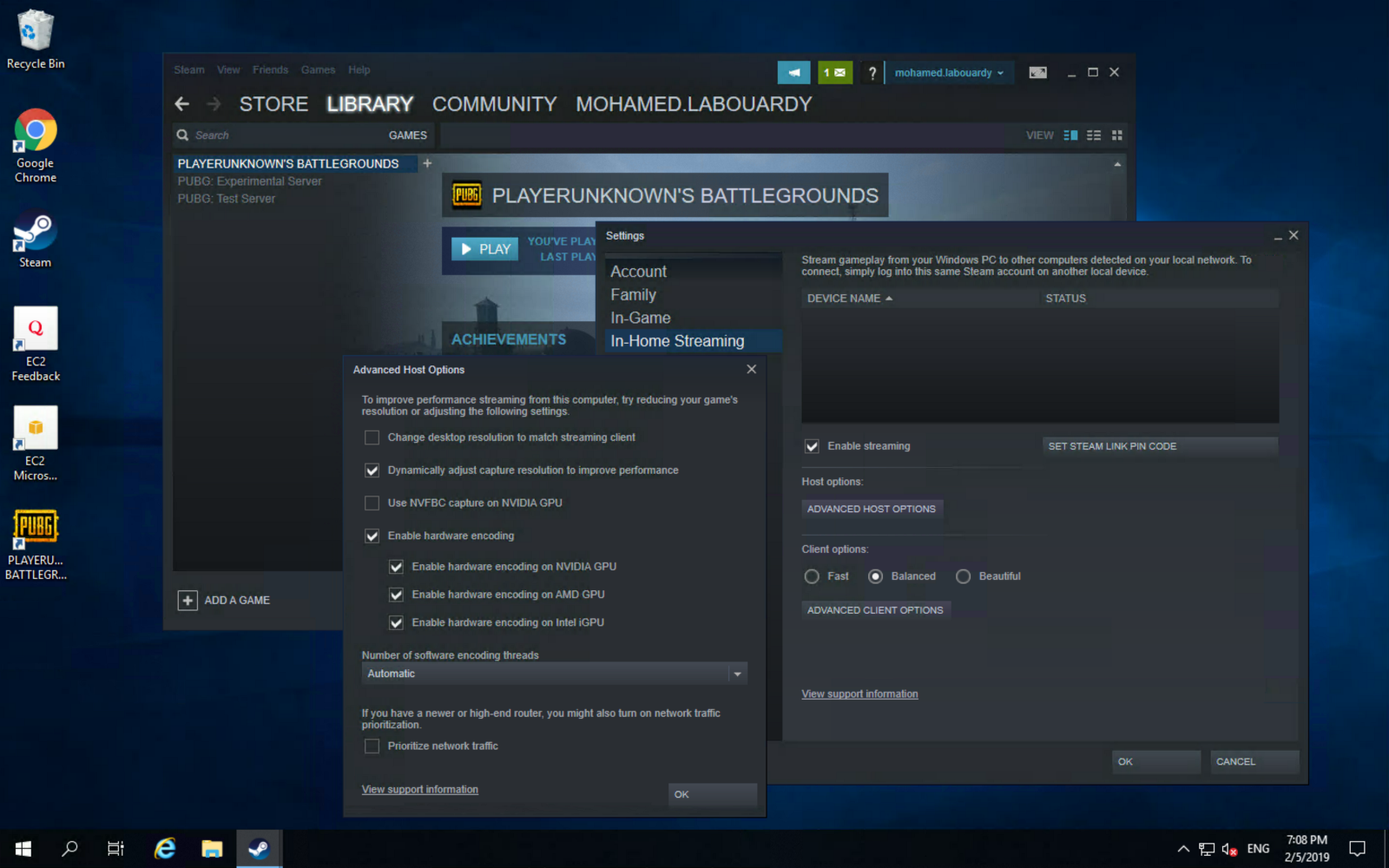
You can take this further, and use Steam In-Home Streaming feature to stream your game from your EC2 instance to your Mac:
Enjoy the game ! you can now play your games on any device connected to the same network:
You might want to bake an AMI based on your instance to avoid set it up all again the next time you want to play and use spot instances to reduce the instance cost. Also, make sure to stop your instances when you’re done for the day to avoid incurring charges. GPU instances are costly (disk storage also costs something, and can be significant if you have a large disk footprint).
Drop your comments, feedback, or suggestions below — or connect with me directly on Twitter @mlabouardy.